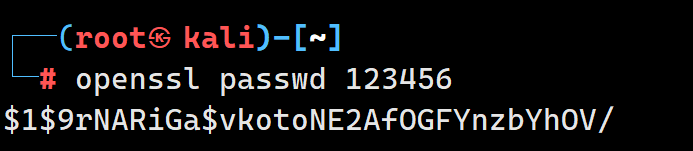
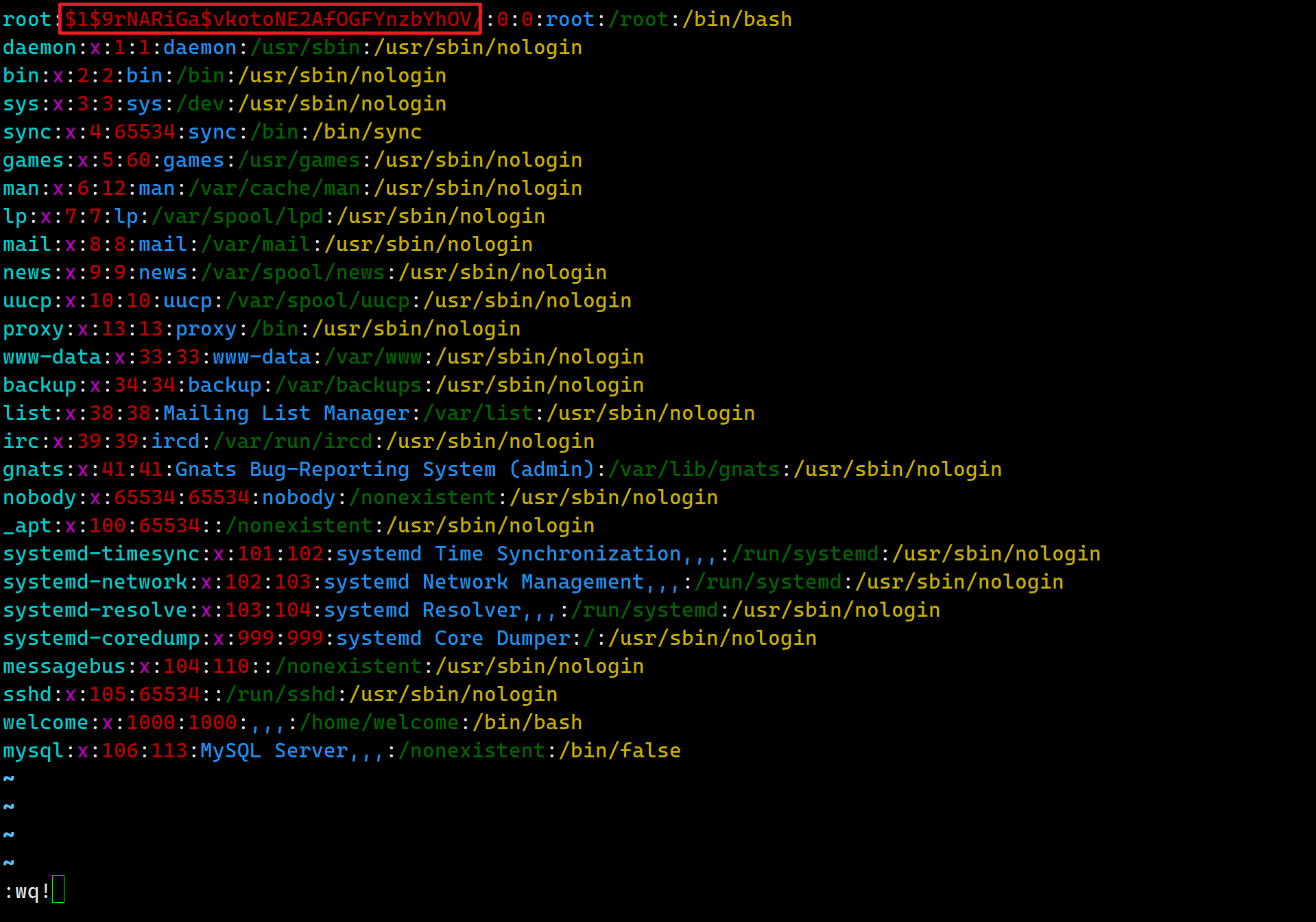
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
70
71
72
73
74
75
76
77
78
79
80
81
82
83
| ┌──(root㉿kali)-[~]
└─# tcpdump -A -n host 192.168.215.173
tcpdump: verbose output suppressed, use -v[v]... for full protocol decode
listening on eth0, link-type EN10MB (Ethernet), snapshot length 262144 bytes
01:14:00.568387 IP 192.168.215.173.45158 > 255.255.255.255.5000: UDP, length 1
E...].@.@.D..........f... 1.r.................
01:14:01.568918 IP 192.168.215.173.45158 > 255.255.255.255.5000: UDP, length 1
E...^B@.@.D8.........f... 4.o.................
01:14:02.569864 IP 192.168.215.173.45158 > 255.255.255.255.5000: UDP, length 1
E...^.@.@.C..........f... 4.o.................
01:14:03.555984 ARP, Reply 192.168.215.149 is-at be:90:0d:14:3a:ef, length 46
............:.......'.........................
01:14:03.570485 IP 192.168.215.173.45158 > 255.255.255.255.5000: UDP, length 1
E..._.@.@.B..........f... /.t.................
01:14:04.571266 IP 192.168.215.173.45158 > 255.255.255.255.5000: UDP, length 1
E..._.@.@.B..........f... i.:.................
01:14:05.572639 IP 192.168.215.173.45158 > 255.255.255.255.5000: UDP, length 1
E...`.@.@.A..........f... s.0.................
01:14:06.573245 IP 192.168.215.173.45158 > 255.255.255.255.5000: UDP, length 1
E...`.@.@.A..........f... s.0.................
01:14:07.575612 IP 192.168.215.173.45158 > 255.255.255.255.5000: UDP, length 1
E...a @.@.Aq.........f... ?.d.................
01:14:08.575261 IP 192.168.215.173.45158 > 255.255.255.255.5000: UDP, length 1
E...a.@.@.@..........f... B.a.................
01:14:09.575737 IP 192.168.215.173.45158 > 255.255.255.255.5000: UDP, length 1
E...b/@.@.@K.........f... >.e.................
01:14:10.576951 IP 192.168.215.173.45158 > 255.255.255.255.5000: UDP, length 1
E...b.@.@.?..........f... j.9.................
01:14:11.577919 IP 192.168.215.173.45158 > 255.255.255.255.5000: UDP, length 1
E...c.@.@.?z.........f... >.e.................
01:14:12.579059 IP 192.168.215.173.45158 > 255.255.255.255.5000: UDP, length 1
E...cb@.@.?..........f... p.3.................
01:14:13.579527 IP 192.168.215.173.45158 > 255.255.255.255.5000: UDP, length 1
E...c.@.@.>..........f... s.0.................
01:14:14.580549 IP 192.168.215.173.45158 > 255.255.255.255.5000: UDP, length 1
E...d~@.@.=..........f... n.5.................
01:14:15.581968 IP 192.168.215.173.45158 > 255.255.255.255.5000: UDP, length 1
E...d.@.@.=..........f... q.2.................
01:14:16.582744 IP 192.168.215.173.45158 > 255.255.255.255.5000: UDP, length 1
E...e3@.@.=G.........f... =.f.................
01:14:17.582799 IP 192.168.215.173.45158 > 255.255.255.255.5000: UDP, length 1
E...e.@.@.<..........f... A.b.................
01:14:18.582829 IP 192.168.215.173.45158 > 255.255.255.255.5000: UDP, length 1
E...fl@.@.<..........f... q.2.................
01:14:19.583656 IP 192.168.215.173.45158 > 255.255.255.255.5000: UDP, length 1
E...f.@.@.
01:14:20.584942 IP 192.168.215.173.45158 > 255.255.255.255.5000: UDP, length 1
E...g.@.@.
01:14:21.584519 IP 192.168.215.173.45158 > 255.255.255.255.5000: UDP, length 1
E...g.@.@.:..........f... n.5.................
01:14:22.585250 IP 192.168.215.173.45158 > 255.255.255.255.5000: UDP, length 1
E...hx@.@.:..........f... o.4.................
01:14:23.586363 IP 192.168.215.173.45158 > 255.255.255.255.5000: UDP, length 1
E...i#@.@.9W.........f... s.0.................
01:14:24.587307 IP 192.168.215.173.45158 > 255.255.255.255.5000: UDP, length 1
E...i.@.@.8..........f... k.8.................
01:14:25.588206 IP 192.168.215.173.45158 > 255.255.255.255.5000: UDP, length 1
E...i.@.@.8..........f... r.1.................
01:14:26.589368 IP 192.168.215.173.45158 > 255.255.255.255.5000: UDP, length 1
E...i.@.@.8..........f... k.8.................
01:14:27.589576 IP 192.168.215.173.45158 > 255.255.255.255.5000: UDP, length 1
E...j.@.@.7..........f... q.2.................
01:14:28.589566 IP 192.168.215.173.45158 > 255.255.255.255.5000: UDP, length 1
E...kF@.@.74.........f... m.6.................
01:14:29.590355 IP 192.168.215.173.45158 > 255.255.255.255.5000: UDP, length 1
E...l4@.@.6F.........f... s.0.................
01:14:30.591045 IP 192.168.215.173.45158 > 255.255.255.255.5000: UDP, length 1
E...l.@.@.5..........f... q.2.................
01:14:31.591903 IP 192.168.215.173.45158 > 255.255.255.255.5000: UDP, length 1
E...m#@.@.5W.........f... p.3.................
01:14:32.592596 IP 192.168.215.173.45158 > 255.255.255.255.5000: UDP, length 1
E...m.@.@.4..........f... k.8.................
01:14:33.593930 IP 192.168.215.173.45158 > 255.255.255.255.5000: UDP, length 1
E...n.@.@.3..........f... p.3.................
01:14:34.594443 IP 192.168.215.173.45158 > 255.255.255.255.5000: UDP, length 1
E...o|@.@.2..........f... @.c.................
01:14:35.594870 IP 192.168.215.173.45158 > 255.255.255.255.5000: UDP, length 1
E...o.@.@.2..........f... >.e.................
01:14:36.595925 IP 192.168.215.173.45158 > 255.255.255.255.5000: UDP, length 1
E...p.@.@.2u.........f... r.1.................
01:14:37.071817 ARP, Reply 192.168.215.149 is-at be:90:0d:14:3a:ef, length 46
............:.......'.........................
|